[ Tinydeal Technology News]Recently, Tinydeallearned from foreign media that multiple applications developed by Microsoft app vulnerabilities on macOS have been exposed to multiple security vulnerabilities. These vulnerabilities allow hackers to exploit the permission framework of Apple’s operating system to illegally access users’ cameras and microphones. Affected software includes Microsoft Office, Outlook, Teams, OneNote, etc.
Cybersecurity organization Cisco Talos disclosed the details of these vulnerabilities, pointing out that hackers can bypass the macOS permission model and achieve user control by injecting specially crafted malicious libraries into six applications: Outlook, Teams, PowerPoint, Excel, Word, and OneNote. Unlawful control of equipment.
According to Apple’s Transparency, Consent, and Control (TCC) framework on macOS, malware needs to obtain the user’s explicit consent for relevant permissions to access the Microsoft app vulnerabilities on macOSand camera. Some malicious programs exploit a process called library injection (or dylib injection on macOS) to gain permissions originally granted to other applications.
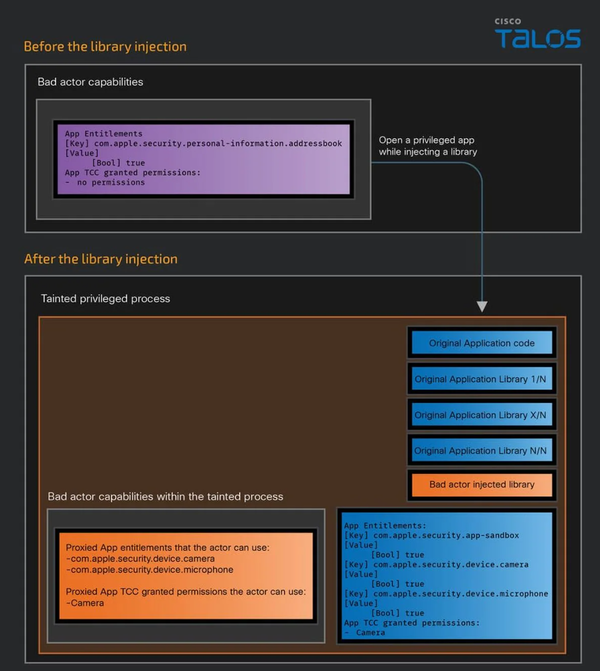
According to Cisco Talos, macOS users with Microsoft apps may be vulnerable to hackers. Hackers can exploit these flaws to record audio by injecting libraries into the applications. Among the affected apps, only Microsoft Excel lacks access to the microphone. Apps like Microsoft Teams can access both the microphone and the camera.
The cybersecurity group reported these vulnerabilities to Microsoft. Microsoft has updated Teams and OneNote to fix the issues. Microsoft has not yet resolved the flaws in Outlook and Office applications.
Cisco Talos criticized Microsoft for disabling library verification. This decision exposed users to unnecessary risks. It bypassed Apple’s runtime protections designed to secure the TCC and permissions model.






